We produce telecom equipment, the equipments will be deployed as infrastructure of telecommunication, internet etc., so it required product high stability, high security. We would not like to see there will be a 911 phone call cannot be reachable since our software bug, or financial exchange be stuck since networking problem which is caused by our software bug.
I recall that one day, Erno Jeges (who is secure coding expert) told us: you have to care your code as care your baby, otherwise you don’t know what your baby will be. So that, we have to deal software security carefully: buffer overflow, print formatting, and integer overflow etc. I’m not expert in this area, but I notice that at least we have to take care of our integer variable first since C/C++ languages handle integers in a very dangerous manner since there are:
- No overflow exception
- No run-time detection if a negative integer is converted to an unsigned value
- No checks whether a larger integer value is put into a shorter variable
That’s why in our source code hides one integer number multiply by one integer number, and leads software fiery crash. Of cause, sometimes, we can rely on static analysis tool such as Klocwork, cppcheck, but not all of problems can be filtered by tool, human shall participate in the process of software creation. As these reason, programmer who is programming in C/C++ language shall be carefully deal with the calculation or convention of integer variable, and it shall be basic knowledge of C/C++ programmer. That’s why I act Longevity Monk who from A Chinese Odyssey here.

It’s time to start the puzzle game, please spot out the bomb which is hiden inside the code, let’s look at this code snippet:
1 2 3 4 5 6 7 8 9 10 11 | |
Could you please tell me is there any problem if you stop here and do not plan to go through this post? Of cause, there is a big problem once assign a negative value to parameter len, for example, we assign the len is -1, the program can be executed in memcpy(dest, src, len), and -1 will be casted to unsigned value 0xffffffff, and lead the program Segmentation fault, this problem is called Signedness bug.
Okay, let’s see another code snippet here:
1 2 3 4 5 6 7 8 9 10 11 12 | |
How about this one, is there any problem? In case of len1 is huge number, and len1+len2 can be overflow to a small number. For example, len1 = 4294967198, and len2 = 100, and then len1 + len2 = 4294967298 (0x100000002). We call this problem is Arithmetical overflow.
one more, this will be easily to spot with previous experience:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | |
If the len is 65535, the s will be 0, and lead segmentation fault during memcpy, we call it Widthness integer overflow. So here we would like to highlight the ranges of integer, we believe professional programmer can deal it well.
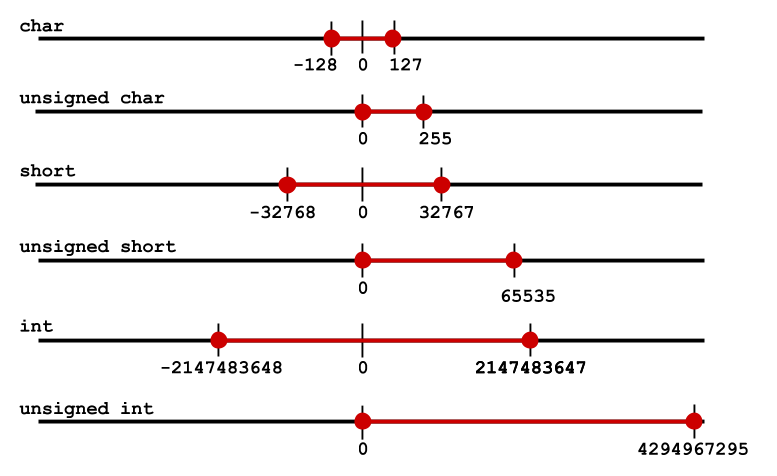
And now it’s time to review you owned source code, is there any same problem? Have you group the integer calculation invoking in some centralized place rather than spread everywhere of your program? Have you clearly understand using variable is 2bytes, 4bytes or 8bytes? signed or unsigned?
Be careful! :\
(Knowledge I learned from Computer Systems: A programmer’s perspective, and emphasize the mindset in secure coding course, if you forget the knowledge, hope this post can remind you pick your book up.)